Earlier this year, Kaspersky researchers discovered a weaponised Word document which utilised a novel infection scheme with a three-stage payload that targeted selected industries in South Korea.
Earlier this year, Kaspersky researchers discovered a weaponised Word document which utilised a novel infection scheme with a three-stage payload that targeted selected industries in South Korea. Initial findings suggested that this was the work of the Lazarus advanced persistent threat (APT) group; further analysis by the Kaspersky Global Research and Analysis (GReAT) team revealed the attack was actually conducted by the Andariel group, a subgroup of the Lazarus APT, based on several telltale signs in its code and means of execution.
The Kaspersky team attribute this campaign to Andariel based on the way the hackers implemented Windows commands and decryption routines malware used in this campaign -- tactical fingerprints that match previous approaches used by Andariel. Two elements of the code overlap with the PEBBLEDASH malware family attributed to the Lazarus group with weak confidence.
Andariel group is a state-sponsored threat actor designated by the Korean Financial Security Institute as a sub-group of Lazarus. The group prioritises attacks on South Korean institutions with an emphasis on financial gain and cyber espionage. From 2017, the Andariel Group shifted their focus to attacks for monetary gain against financial institutions as well as a previous operation that compromised ATMs in South Korea.
“While the attacks of Andariel are primarily targeted towards institutions in South Korea, organisations irrespective of geographical borders must nevertheless remain vigilant against cyberattacks and preemptively prevent the weakest link - the human element in employees - from potentially compromising security”, Seongsu Park, Senior Security Researcher, Kaspersky GReAT APAC noted.
Ransomware - Wolf in Word’s Clothing
Kaspersky GReAT uncovered the aforementioned suspicious Word document on VirusTotal which had an innocuous file name ‘Form of participation application.doc’ written in Korean script. While this attempt was discovered in April 2021, the third stage payload has been spread by the threat actor from the middle of 2020 onwards.
Clicking and opening the Word doc activates the first of a three-stage payload - the launch of a malicious macro that is executed in the background while a decoy document is displayed to the user. In the first stage, the executed macro runs a hidden HTML Application (HTA) file which contains the second stage payload. This payload communicates with a remote command-and-control (C2) server which then prepares the third-stage payload.
Cunningly, the second and third stage payloads mimic a legitimate browser by using the Internet Explorer icon and corresponding file names. Once the third stage is launched, it checks the system if it is a sandbox environment by checking for the presence of specific modules.
If the coast is clear, the third stage payload sends a message to the same C2 server. If it gets a positive message string from the C2 server, in effect a go ahead to proceed, the deployed malware runs and can then conduct backdoor operations that include executing Windows commands, connecting to a given IP address, listing files and manipulating them as well as taking a screenshot. This effectively gives the threat actor unimpeded access to the compromised system.
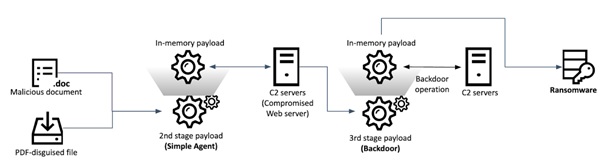
Infection procedure
One of the targeted victims in South Korea encountered a custom-made ransomware attack by the threat actor that is controlled by command line parameters rather than something off-the-shelf. If specific criteria are fulfilled, the ransomware then employs an AES-128 CBC code algorithm to encrypt almost all of the files on the target machine, save for system-critical files, to allow the ransomware victim to still interact with the machine and potentially pay the ransom. It also leaves a ransom note on the desktop and in the startup folder to prompt the victim to pay the ransom in Bitcoin.
Evidence also showed that Andariel used another infection vector that mimicked a PDF file. The original file was not available for analysis, though its existence was extrapolated from artefacts gleaned from the exPDFReader tool made by a South Korean company. The infection path for this variant is unclear due to lack of evidence, though speculation is that it either relied on a software exploit or that it masqueraded as a legitimate file, fooling users into opening it.
To prevent similar attacks such as that employed by Andariel, Kaspersky experts advise the following:
- Ensure staff at all levels of the organisation are equipped with basic cybersecurity training with regular refresher courses to ensure awareness against potential phishing and social engineering attempts and, in this particular scenario, suspicious files
- Rigorously highlight and enforce cybersecurity policies throughout the organisation.
- Empower Security Operations Center (SOC) team with the latest threat intelligence. One potential, comprehensive solution is Kaspersky Threat Intelligence reporting services that offers constantly updated, in-depth intelligence data enabling SOC teams to stay abreast of ongoing cyberthreats.
- Financial industry organisations require multi-layered protection solutions to protect against both generic and targeted attacks. Kaspersky Finance Services Cybersecurity services leverages on Kaspersky’s two decades of experience at the forefront of cybersecurity with industry-specific tailored security solutions to mitigate risk, detect attacks at an earlier stage, deal with live attacks and enhance protection from future attacks.
More information about this activity can be found at Securelist.
About Kaspersky:
Kaspersky is a global cybersecurity company and digital privacy founded in 1997. Kaspersky’s deep threat intelligence and security expertise is constantly transforming into innovative security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialised security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky technologies and we help 240,000 corporate clients protect what matters most to them. Learn more at www.kaspersky.com.




