What do you suppose the click-through rate is for links received by men in dating app messages from attractive women? Take a guess — 1%? 5%? 15%? According to research conducted by Inbar Raz of PerimeterX, it’s an incredible 70%! Two out of three men actually click on these links, which makes it without doubt the best conversion rate in the world. Take another guess: What could possibly go wrong?
Inbar Raz started his research with building the perfect Tinder profile. This subject is surprisingly well researched — I’m talking mathematically researched. There’s a lot of guidelines on that, and even an interview with Tinder CEO Sean Rid in which he describes what kinds of photos can actually get you the most matches. Here’s a short list of the kinds of photos that work the best:
- a photo taken by a professional photographer;
- a photo with an animal;
- a photo of you doing sports or some hobby;
- something official or at work;
- something silly or creative.
Love at first sight
About a year ago Raz traveled to Copenhagen, Denmark, to speak at a security conference. When he arrived, he turned on Tinder and within an hour had eight matches with beautiful women. One of them sent him a message in Danish, with a link in the end. A lot of more matches followed, and a lot of messages too. The messages were almost identical, with only the last four characters in the link different between them.
Naturally, Raz was suspicious that these beautiful women might in fact be bots and started researching his fishy “matches.” First, he noted that the 57 matches had between them only 29 places of education, 26 workplaces, and 11 professions — most of them claimed to be models. Moreover, although all of the bots except for one had places of education in Denmark, almost all of them listed employment in the United Kingdom, mostly in London.
After that, Raz checked the profile information of the matches. They turned out to be combinations of stolen identities: There were links to Facebook and Instagram accounts that didn’t match the names and pictures in the Tinder profiles.
Getting to know bots better
A few months passed and Inbar Raz went to another security conference in Denver, Colorado. Guess what? He got another bunch of Tinder matches, again mostly fake. Some of the matches in Denver were more advanced chat bots — they didn’t sent a fishy link immediately; they tried chatting first. Raz asked them intricate questions to probe how interactive these chat bots really were. Turned out, not very: the chats went by hard-coded script, no matter what questions and answers the researcher provided. And of course, they all ended either with an invitation to continue the conversation in Skype or with a link.
This time, Raz decided to check out the links the bots were sending him. The links led to websites that redirected to other websites that redirected to still another website. And the final destination was titled “This IS NOT a dating site” and carried the following warning: “You will see nude photos. Please be discreet.” Whatever discreet is supposed to mean in such circumstances.
Fast-forward a couple of months and Raz was attending yet another conference, the Chaos Communication Congress in Hamburg, Germany. This time, one of his bot matches had a link in its profile that led to a website titled “Better than Tinder,” which featured large nude photos right on the main page.
Chasing the puppet master
A month later, Raz visited his next security conference, in Austin, Texas. He turned on Tinder, and sure enough, more matches sprung up. After his previous investigation, Raz didn’t have any expectations and was sure these matches would be bots. So, chatting with yet another bot, he didn’t even pretend he was talking to a real person. Indeed, the conversation went by the script, and in the end Raz received an invitation to continue the chat in Skype with juicyyy768.
The account name reminded him of the bot that invited him to Skype when he was in Denver — the name followed the same formula: a word with the last letters repeated several times and three digits at the end. Raz created a disposable Skype account and chatted with the bot in Skype. After another scripted dialogue, the bot asked Raz to create an account on a photo-sharing website. Needless to say, the website demanded a credit card number. By now, you probably have a hunch where this is all going.
The next step was tracking the infrastructure of the bot empire. Raz checked the IP address of one of the websites he had received a link to in his early chats with Tinder bots. A list of shady domain names was associated with the IP. The websites’ names were related to sex, or Tinder, or something along those lines. Raz started to check the registration info for these domains, but most of the domains had been registered anonymously.
However, checking all 61 domains yielded a bit more information. Some of them were registered by different means, and several even had some registration information indicating a name, phone number, address (in Marseille, France), and e-mail. All of that turned out to be fake, but it still gave Raz some new leads to follow and dots to connect.
Using a website called Scamadviser.com, which checks how safe other websites are to buy from, Raz was able to link bot campaigns from different cities located on different continents to the same e-mail address, *****752@gmail.com, which he obtained from the domain registration info. The owner of this address uses several fake names, different fake phone numbers, and different addresses. Consistent elements were the addresses being in Marseille and the word-plus-three-digits formula for nicknames. Raz didn’t manage to find the scammer’s real identity; unfortunately, whoever it is he’s good at hiding.
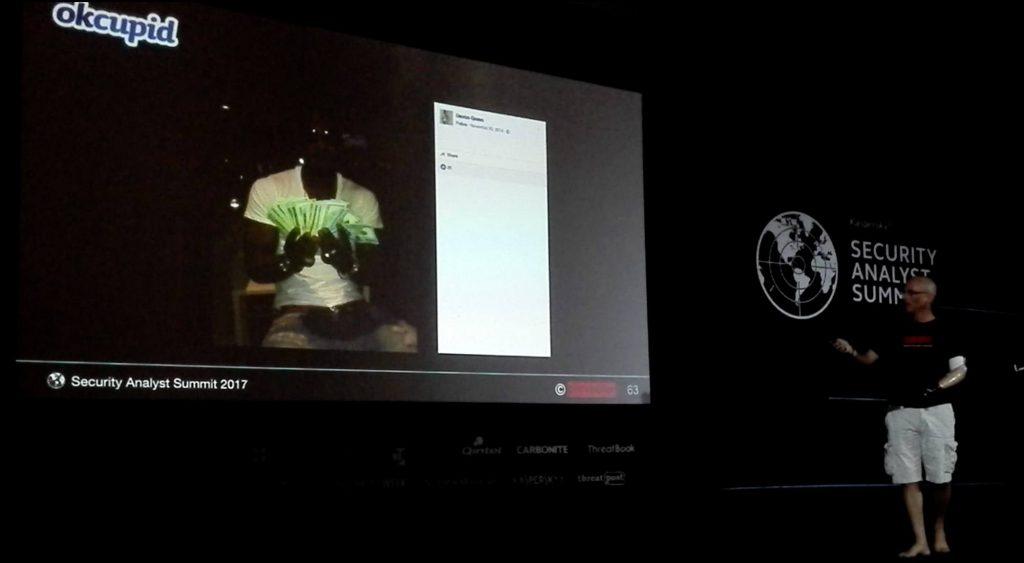
After that, Raz switched to another platform, OkCupid, to check if there were bots there as well. And indeed there were. They were not as well-crafted as the Tinder bots, and the websites they led to did not look very professional. As further research showed, the person behind this small bot empire also wasn’t nearly as good at operational security as *****752 was. After checking a bunch of websites, Raz discovered first an e-mail address, and after that the name of the scammer, and then even his real Facebook account with nice photo of the swindler holding stacks of money in his hands.
Don’t fear the Tinder
OK, so there are bots in Tinder. So what? Well, these bots aren’t just wasting your time or getting your hopes up for no reason. They are phishing for your credit card data, and, as we mentioned at the beginning of this post, the click-through rate for the links they send is amazingly high. That means a lot of men actually go to those websites, and some even enter their banking data there — looking for their beautiful matches. Poor them.
None of that means you have to stop using Tinder, or OkCupid, or whatever other dating app you like. It just means that you have to be prepared and careful.
- Don’t click on any links a stranger sends you. There is no legitimate reason in the world for a “match” to send you a link. That said, do check profile details. If your new match has links to profiles with different names, something is probably wrong.
- Be aware — and wary. There are bots pretty much everywhere on the Internet. At least for now they are not very sophisticated, so it’s reasonably easy to distinguish a real person from a bot. Just don’t lose your head at the prospect of a gorgeous match. Try changing the subject and see if they can follow along, for example.
- Don’t date bots. Please. And take our quiz about phishing to learn about more scammers’ tricks.
 #TheSAS2017
#TheSAS2017



 Tips
Tips