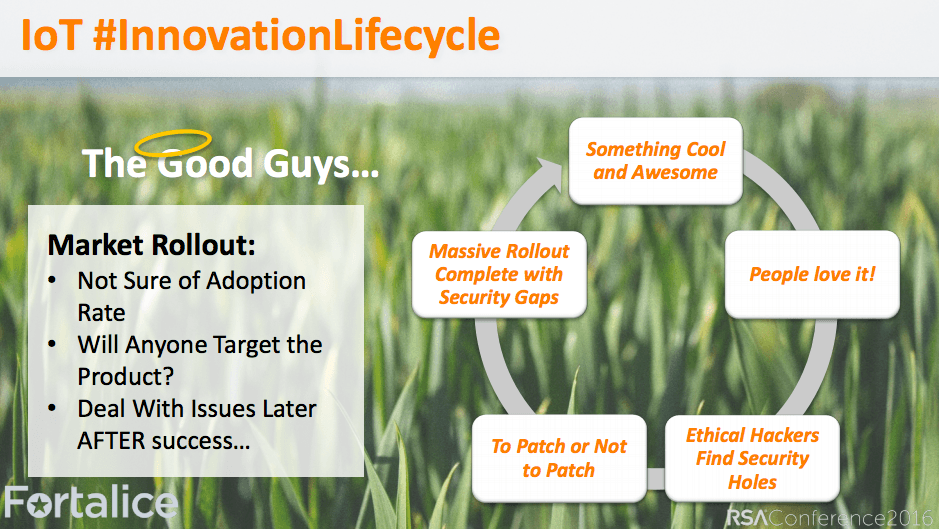
When a product is built, the manufacturer typically has a lifecycle in mind in regards to how long a consumer will ideally use the device. For example smartphones are something that users typically swap out every two years and automobile manufacturers will look at car buyers trading in their car every five or so years.
The problem with this though is that humans don’t act the way these types of purchasing patterns presuppose. One would only need to look at a used car dealership or peruse eBay to find an aftermarket for cars or phones. Ok, eBay is enough for both.
This secondary sales market is also something that is going to become more important for manufacturers to think about as the IoT grows. Why you ask? Since many devices have a finite timeline in a company’s sell-sheet, they are not supported after their ‘expiration’ date, and usually, that’s exactly the time when they bypass the trash and head straight to the aftermarket.
Chances are that those who buy these IoT devices from their previous owners could very well end up with something that’s not longer protected from any vulnerabilities that would be found afterwards. And there certainly would be a lot of those vulnerabilities, as both white hat and black hat hackers are constantly searching for them.
We have already seen many devices connected to the Internet fall susceptible to a hack due to software that is used to connect to the web, which ironically is also past it’s prime. Items compromised range from baby monitors to air conditioners to automobiles. Sadly if something connects to the web, it can be hacked. And there are IoT search engines to make it happen faster.
When hacking air conditioners leads to blackout https://t.co/LSxYAgBSI2 #TheSAS2016 https://t.co/LSxYAgBSI2 #infosec pic.twitter.com/5koCkAcwGb
— Kaspersky (@kaspersky) February 18, 2016
Overall, we also know that cybersecurity usually comes last when companies plan out their products and find ways to make them connected. Something has to give, right?According to Todd Inskeep of Booz Allen Hamilton, companies need to start looking at building trust when it comes to these devices and their connectivity. At this year’s RSA Conference, he gave a presentation entitled Cyber Wars: The Trust Awakens.
During the talk, he discussed the need for a fundamental shift in product development. All stakeholders should be involved in this shift, from concept to R&D to marketing and sales, along with everyone in between. The reason for this is that without accounting for the worst case, should it happen, you lose customer trust.
In theory, companies would operate similar to the military, which prepares in advance for all of the scenarios that can play out. They also operate systematically with their process. To put it into marketing speak, their brand is operating as a cohesive unit. Also, many of the mantras of the branches of the military are pretty engrained into the memories of most Americans.
Medicine under fire: how to hack a hospital https://t.co/QcmY3IlWGR #TheSAS2016 #Healthcare #medicalsec pic.twitter.com/Cil0ueabag
— Kaspersky (@kaspersky) February 11, 2016
While change is something that we can all agree needs to happen with companies thinking of security, let’s be honest — it could take a long time. So what can you do?
When it comes to looking at purchases, you will always have choices as to what suits your need for a given moment. For connected devices, I’d implore you to ask yourself the following questions:
- Do I really need to have this connected to the web?
- What is this company’s reputation on security?
If you answered #1 as no, move along and get another product. As for #2 a Google search should help you with some of the research on the company. If you want to stay up to date with the latest IT industry news, be sure to head over to Threatpost.
 breach
breach