As unpleasant as it is to see a ransomware message pop up on your monitor, WannaCry or ExPetr/NotPetya are not worst-case scenarios. Researchers demonstrated far more physical cyberattacks at the Black Hat hacking conference.

Thousands of factories around the world employ robots whose mechanical manipulators move boxes around, drill through parts, and perform other actions by following preprogrammed routines. These robots are quite complex, consisting of a computer (used for monitoring by an operator), a controller, and a mechanical manipulator. A program with logical operations, such as “lift the box” or “turn the arm,” is created on the control computer, and the controller breaks it down into a series of smaller steps.
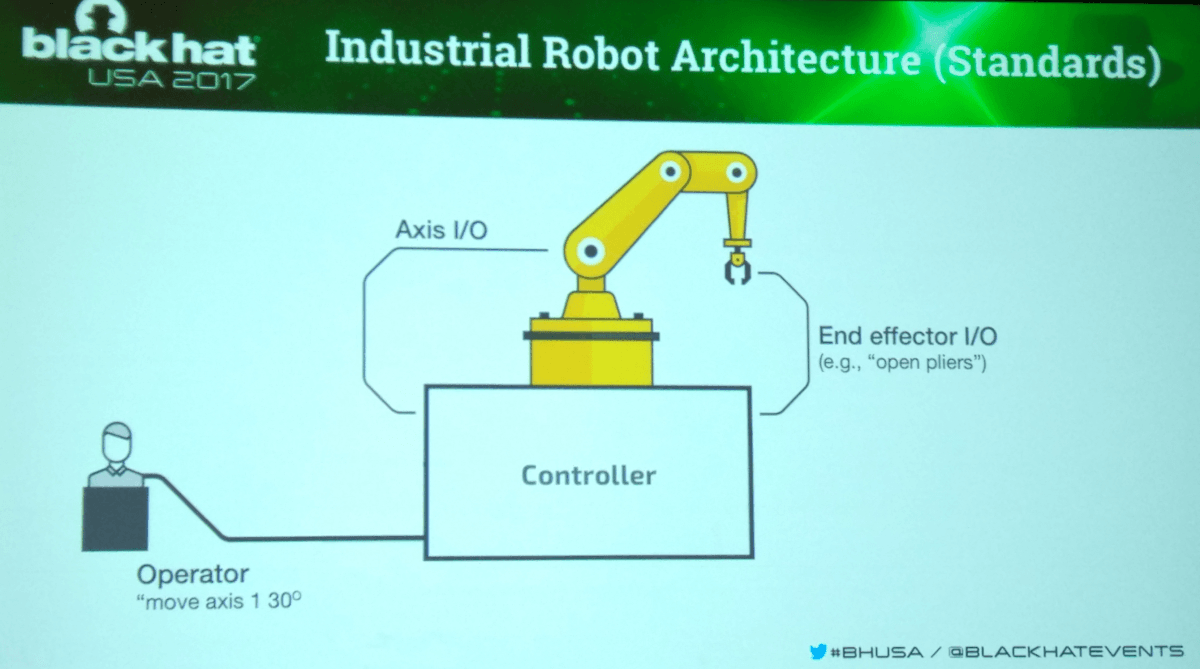
The process is intricate, with many factors. For example, a box needs to be lifted smoothly and only to a certain height, and the pressing force of the “fingers” must remain at a certain value to hold the transported part firmly. The controller stores configuration files that contain data for applying a certain voltage to servomotors at a clearly specified moment, thus allowing the manipulator to lift the box correctly.
Managing cybersecurity
The developers of industrial robots have invested substantial efforts to ensure their inventions operate safely. Various safety devices, logical checks, and user manuals secure both factory and operators against physical damage and injury in case of operation problems or robot failures. At the same time, factory infrastructure is assumed to be “friendly”; a robot fully trusts its control computer.
However, that assumption is not always fair. Researchers have discovered that some robots are directly connected to the Internet (for example, for receiving updates from the manufacturer or sending telemetry to company headquarters), or to an insufficiently isolated factory Wi-Fi network. This enables malefactors to discover robots with the help of a dedicated scanner.
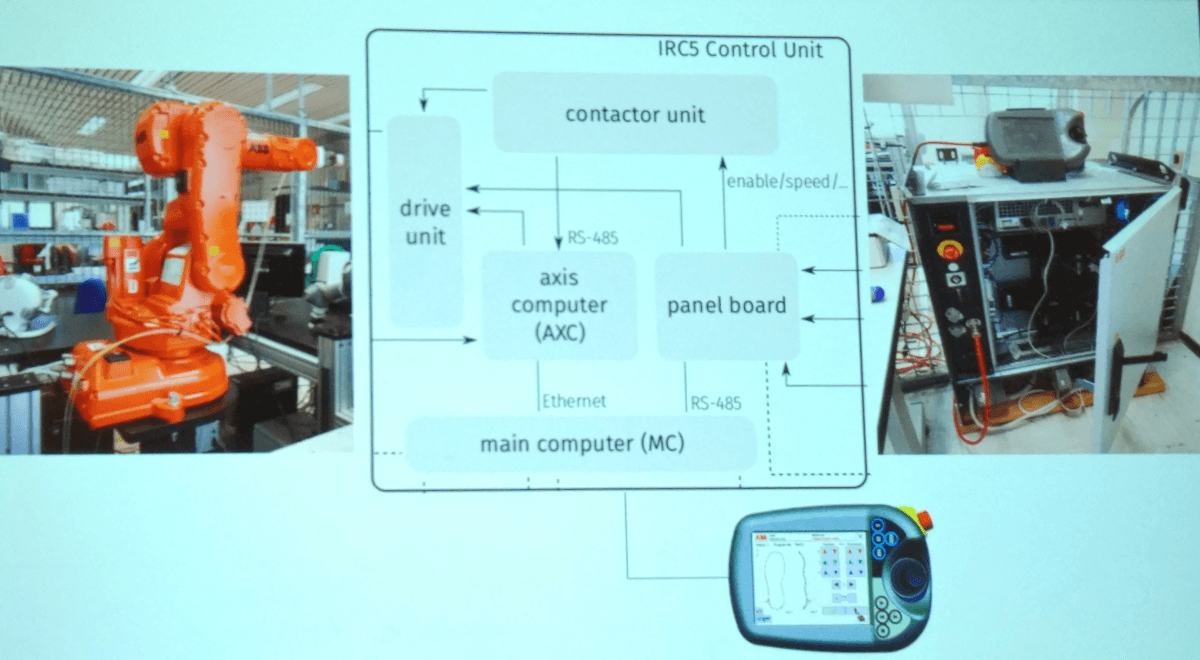
The robots are easy prey. With no encryption used when updating firmware, no digitally signed firmware at all, and default user names and passwords used, anyone who finds a robot’s IP address can modify its configuration files and change its operation logic.
Why hack a robot?
Depending on a hacker’s goals, these opportunities can be used for both espionage (downloading existing configuration files to discover manufacturing secrets) and sabotage. Researchers have demonstrated a crafty attack on a robot that was supposed to draw straight lines (in real-life applications, it could perform electric-welding). Hacked, the robot slightly shifted its manipulator by just a fraction of a millimeter, an error that was imperceptible to the naked eye but would render the resulting product defective. The robot’s programming wasn’t modified; the only thing affected was the controller’s parameters.
Other attacks remain hypothetical, but some are dangerous for the operator. A movable robot can be reprogrammed with altered movement threshold values, for example, and that would be catastrophic.

In the short term, protection against such attacks comes down to increasing the security of existing robots to make them less accessible to the outer world as well as applying manufacturer patches that close known cybersecurity holes. In the longer term, robot manufacturers need to find new approaches and update their production standards, prioritizing not only requirements for physical safety and electrical safety but also cybersecurity. It is worth noting that Kaspersky Lab offers critical infrastructure security solutions to accomplish those goals.
 black hat
black hat

 Tips
Tips