UPDATE: A previous version of this article stated – citing a list on Github – that users on a site called HideMyAss were affected by Heartbleed. A spokesperson from that site reached out to us claiming that their users are not affected, and we removed them from the list of affected sites accordingly.
UPDATE #2: The post is updated with the list of affected services which officially recommend to change users’ passwords.
You know a security vulnerability is a serious one when NPR’s David Green leads into the 8 AM hour of Morning Edition talking about it. Such was the case yesterday morning, with the story of a serious encryption flaw – dubbed Heartbleed – in OpenSSL, perhaps the most widely deployed encryption library on the Internet. If you’re a bit confused about what this all means, don’t worry, I am going to attempt to unpack the whole story in the next 500 words or so.
When you establish an encrypted connection to a website, whether it’s Google, Facebook, or your bank’s online branch, the data is encrypted using the SSL/TLS protocol. Many popular web servers utilize the open-source OpenSSL library to do this job for them. Earlier this week, the maintainers of OpenSSL released a fix for a serious bug in the implementation of TLS feature called “Heartbeat,” which could potentially reveal up to 64 kB of server memory to an attacker.
In other words, the flaw could have enabled anyone on the Internet to read the memory of a machine that’s protected by a vulnerable version of the library. In the worst-case scenario, this small block of memory may contain something sensitive – user names, passwords, or even the private key which is used by the server to keep your connection encrypted. In addition, exploiting Heartbleed leaves no traces, so there is no definite way to tell if a server was hacked and what kind of data was stolen.
Here’s the good news: OpenSSL fixed the bug. Here’s the bad news: there is no way to guarantee that those sites and services affected by Heartbleed are implementing the patch that mitigates it. More bad news: apparently the bug is pretty easy to exploit and may have existed for as long as two years. It means that the security certificates of many popular sites may have been stolen, as well as sensitive user data, including passwords.
The action plan for the user
Update:Mashable collected the list of official PR responses from affected web services. To save your time on table reading and certificate checking (more on this below), you can simply change your password on all these sites: Facebook, Instagram, Pinterest, Tumblr, Yahoo, AWS, Box, Dropbox, Github, IFFT, Minecraft, OKCupid, SoundCloud, Wunderlist. Use a unique password for each site!
- Check if your favorite site was vulnerable. There are online tools to check the presence of the vulnerability, but you also need to know if it was present before. Luckily, there is a long list of popular websites that were checked against the vulnerability. Good news: PayPal and Google are unaffected. Bad news: Yahoo, Facebook, Flickr, Duckduckgo, LastPass, Redtube, OkCupid, 500px and many others was vulnerable. Get ready to act if you have an account on those vulnerable sites;
- Check if the site is vulnerable now. There is a simple tool for that.
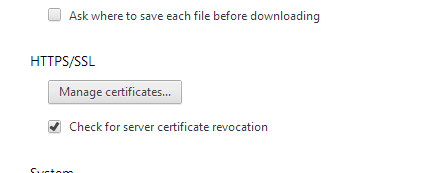
- When site owners fix the bug, they’ll need to consider re-issuing site certificates as well. So get ready to monitor server certificates and make sure you’re using a new one (issued on April 8th or later). To do this, enable the certificate revocation check in your browser. Here is the sample from Google Chrome settings:
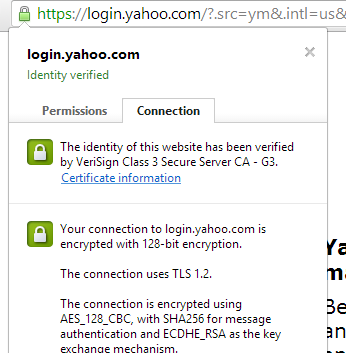
- This will prevent your browser from using old certificates. To check the certificate issue date manually, click the green lock in the address bar and click the “information” link on the “Connection” tab:
- The most important step – when the server is patched and certificate is updated, is to change your password immediately. Use this opportunity to revise your password policy and start using simple to remember yet strong passwords. You can check, if your new password is good using our Password Checker.
 account security
account security