What do e-mails with headings “You’ve won a million dollars” and “Your account is blocked” have in common? They’re almost always signs of a scam. Their aim is to convince the recipient to follow a link to a phishing website and enter confidential information: login and password or bank account details. Here’s how to spot phishing and protect yourself.
1. Check e-mails carefully
When you receive an e-mail, don’t rush to reply or follow its instructions. The first thing you should do is look for telltale signs of phishing. What are the red flags?
- A dramatic subject line. Common themes include large money transfers, financial compensation, hacked or blocked accounts, and fraudulent transactions — attention-grabbing topics likely to trigger an emotional response, often playing on greed or fear.
- Stress on the seriousness of the situation. Phrases like “Final notice!” or “Only 3 hours left” as well as excessive use of exclamation points are meant to make you hurry, panic, and lower your guard.
- Mistakes, typos, and strange characters in the text. Some criminals really do struggle with English, although attackers sometimes purposefully make mistakes like “milion” or use letters from different alphabets in an attempt to bypass spam filters.
- Inconsistent sender address. An e-mail address with a load of random letters and numbers or the wrong domain name are sure signs of forgery when a sender claims to be writing from a large organization.
- Links in the e-mail if it contains them — or the website they lead to, to be more precise. You can check a link by hovering your cursor over it and reading the address carefully. Criminals bet on victims not paying enough attention to detect slight changes made to the names of well-known companies or brands — think sumsung.com or qoogle.com. Check each link carefully.
Such checks should be enough in most cases to spot an e-mail sent as part of a mass phishing scam. However, senders’ names and addresses can be forged, links can be shortened to make them unreadable, and chains of automatic redirects can be set up to lead from less suspicious Web addresses to the actual phishing website. That’s why it’s best to avoid following links sent in e-mails altogether if possible — unless it’s one you asked for. For example, if you get a notice that appears to be from a bank or online store, call the bank or store to confirm.
You can also check if a prize is real by using a search engine to look up the official website of the company supposedly awarding it. Then you can check for prize information there. Those are just a few examples, but our advice is really the same regardless: If you want to check a link from an unsolicited letter, try to do so in a roundabout way.
2. Keep your guard up in messaging apps or on social networks
E-mail isn’t the only thing you need to be careful with. The messages you receive in messaging apps and in social networks have just as much potential for danger; you can find malicious links in friends’ posts on Facebook, in comments posted by fake brand ambassadors on Twitter, or in DMs on Discord.
Treat banners with caution as well; the images they display may have nothing to do with the website they take you to. The platforms where banners are posted usually don’t control what users see or where they’re redirected. Even a perfectly reputable website can serve ads that lead to phishing websites.
What can you do? As with e-mails, check every link carefully, and if possible don’t click on them at all.
3. Stop and think before entering bank account info
Bank card details are particularly sensitive because they provide direct access to your money. That’s why, regardless of how you reached a website, you should double-check where you really are one last time before entering those details.
First, take a close look at the address. You’re looking for the same red flags: typos, numbers instead of letters, hyphens in unexpected places, and strange domain names. If you see anything like that, leave the website and try entering the address manually.
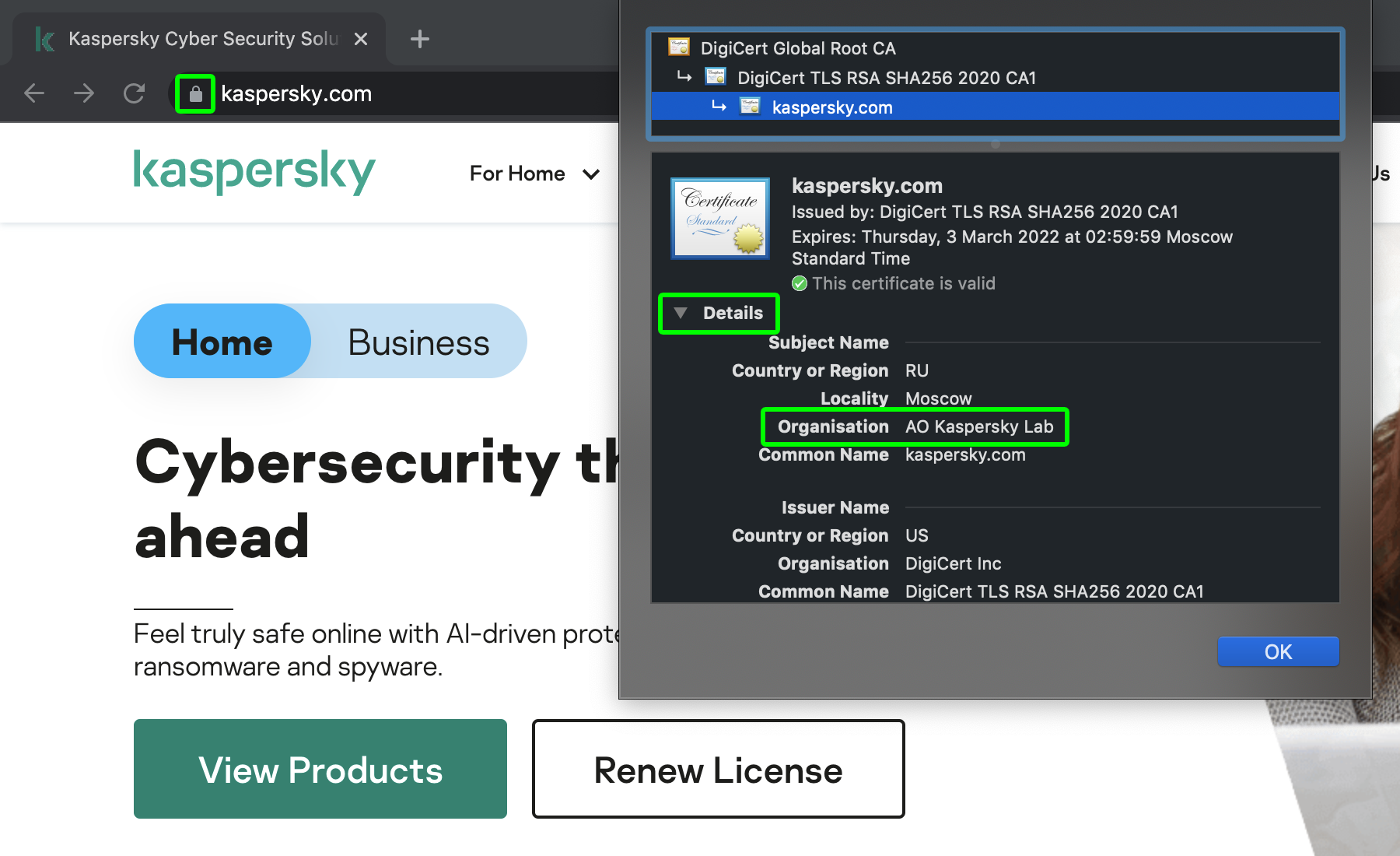
Then, staying in the address bar, click on the padlock icon at the left. The padlock is no guarantee of security, but from it you can learn more about who owns the website (browsers have different names for relevant tabs, such as Certificate or Connection secure).
If you do a lot of online shopping, including purchases from smaller companies and private sellers, we recommend using a separate card. Keep a small amount of money on it and transfer money to it right before you need it. That way, even if the card details are stolen, you won’t lose a large amount of money.
4. Use different passwords
If you use the same password for different accounts, even if it’s a very reliable password, you risk having all of your accounts compromised if you enter it on a phishing website at some point. It’s important to use a unique password for each website and app.
If you find it difficult to come up with and remember dozens of new passwords for every pizza place and online store, use a password manager to create, manage, and use them.
A password manager also acts as an additional check to prevent phishing. If you open an app or site and find it hasn’t automatically filled in your login and password, then you’re probably looking at a fake. It may look the same as the real website to a human, but if it has a different address, the password manager won’t fill in account credentials.
Second, password managers can generate hard-to-hack passwords.
Third, some password managers have useful additional features. For example, Kaspersky Password Manager checks your passwords and notifies you if they’re weak, used for different accounts, or already in a database of compromised passwords.
5. Set up two-factor authentication to protect accounts
Many phishing attacks aim to hijack accounts, but even if attackers get your login and password, you can still stop them from logging in to your account, by setting up two-factor authentication wherever possible. Once you’ve done so, you’ll need an additional temporary verification code to log in. You’ll receive it by e-mail, text, or in an authenticator app. Attackers won’t get one.
Keep in mind, however, that phishers can also create fake login pages that also request one-time, two-factor authentication codes. That’s why it’s better to protect important accounts using hardware-based authentication with a USB key such as YubiKey or Titan Security Key by Google.
Some authenticators use NFC and Bluetooth to connect to mobile devices. The advantage of using a hardware-based security key is it’ll never disclose the secret on a fake website. A website needs to send the right request to get the right answer from the authenticator, and that’s something only the real website knows how to do.
6. Use reliable protection
It’s certainly hard to be on constant lookout for red flags and to check every single address, link, and so on. But it’s a task you can automate, and you can rely on security solutions such as Kaspersky Security Cloud to protect against phishing. The cloud-based protection will notify you in time if you try to go to a malicious page and will block the threat.
 tips
tips