Just a few hours ago, a global ransomware outbreak began, and it looks to be as big as the WannaCry story that broke not so long ago.
Those few hours were enough for several large companies from different countries to report infection, and the magnitude of the epidemic is likely to grow even more.
It’s not yet clear what exactly the new ransomware is. Some thought it might be either some variation of Petya (be it Petya.A, Petya.D, or PetrWrap), or that it could be WannaCry (it’s not). Kaspersky Lab experts are now investigating this new threat, and as soon they come up with solid facts, we’ll update this post.
This appears to be a complex attack which involves several attack vectors. We can confirm that a modified EternalBlue exploit is used for propagation at least within corporate networks. More technical info on the attack.
For now, know that Kaspersky Lab’s products detect the new ransomware using Kaspersky Security Network (KSN) with a verdict UDS:DangerousObject.Multi.Generic. Here’s what we recommend our customers do:
-
-
- Make sure that the Kaspersky Security Network and System Watcher components are turned on.
- Manually update the antivirus databases immediately. It’s also worth updating them several times in the next few hours.
- As an additional means of protection, you can also use the AppLocker feature to disable execution of a file called perfc.dat and the PSExec utility from the Sysinternals Suite.
- Install all security updates for Windows. The one that fixes bugs exploited by EternalBlue is especially important. Here we explain how to do it.
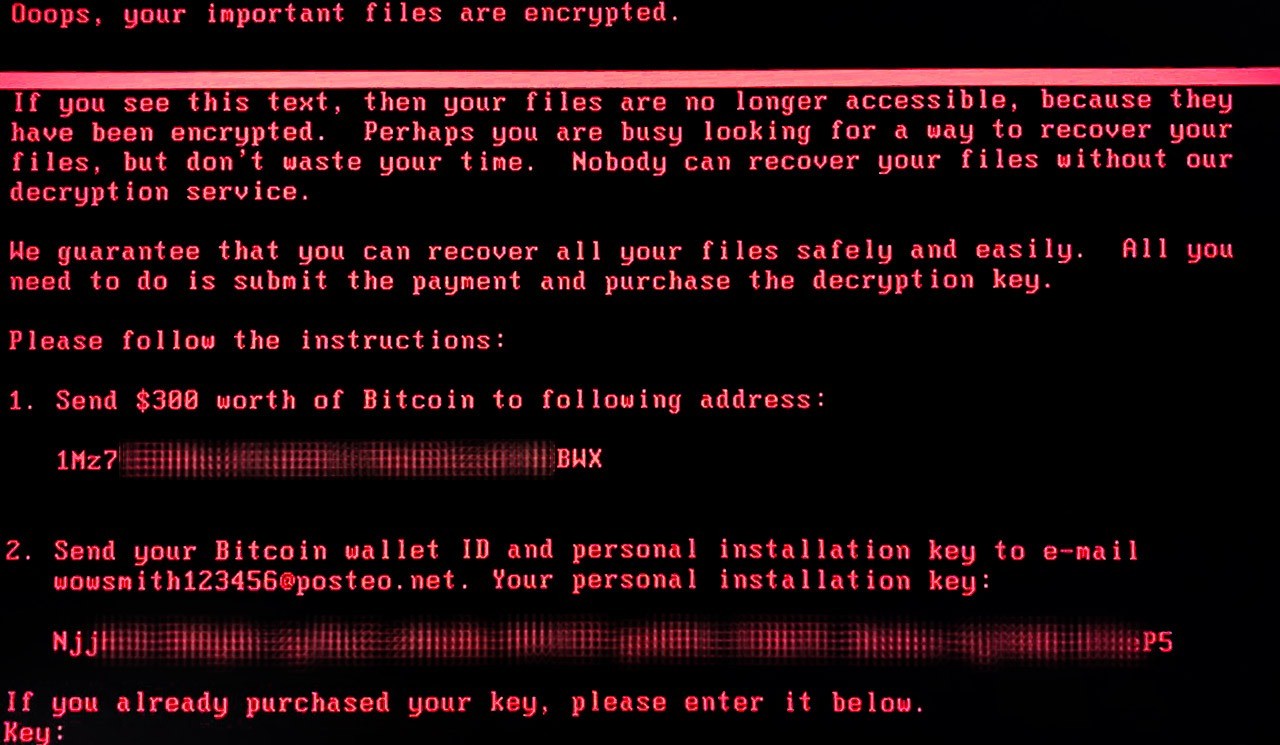
According to an update seen in Motherboard, German email provider Posteo has shut down the e-mail address that was supposed to be used by victims to contact blackmailers, confirm bitcoin transactions and receive decryption keys. What this means is that victims who would look to pay the criminals can no longer get their files back. At Kaspersky Lab, we do not advocate paying the ransom, and in this case it seems to be pointless anyway.
-
Update: More than that, our experts’ analysis indicates there was never much hope for victims to recover their data.
Kaspersky Lab researchers have analyzed the high-level code of the encryption routine and determined that after disk encryption, the threat actor could not decrypt victims’ disks. To decrypt, the threat actors need the installation ID. In previous versions of seemingly similar ransomware such as Petya/Mischa/GoldenEye, this installation ID contained the information necessary for key recovery.
ExPetr (aka NotPetya) does not have that installation ID, which means that the threat actor could not extract the necessary information needed for decryption. In short, victims could not recover their data.
Don’t pay the ransom. It won’t help.
 ransomware
ransomware


 Tips
Tips