Modern antiphishing and antispam solutions increasingly draw on a variety of machine-learning technologies. Using neural networks to analyze text makes them hard to fool, so attackers have turned to a simple but effective trick: placing the text in a picture. They then embed the image in a message body using Base64 encoding (typically, images in e-mail messages are hosted on an external website, and mail clients don’t load pictures in letters from outside the company). Most such letters are after users’ Microsoft Office 365 credentials.
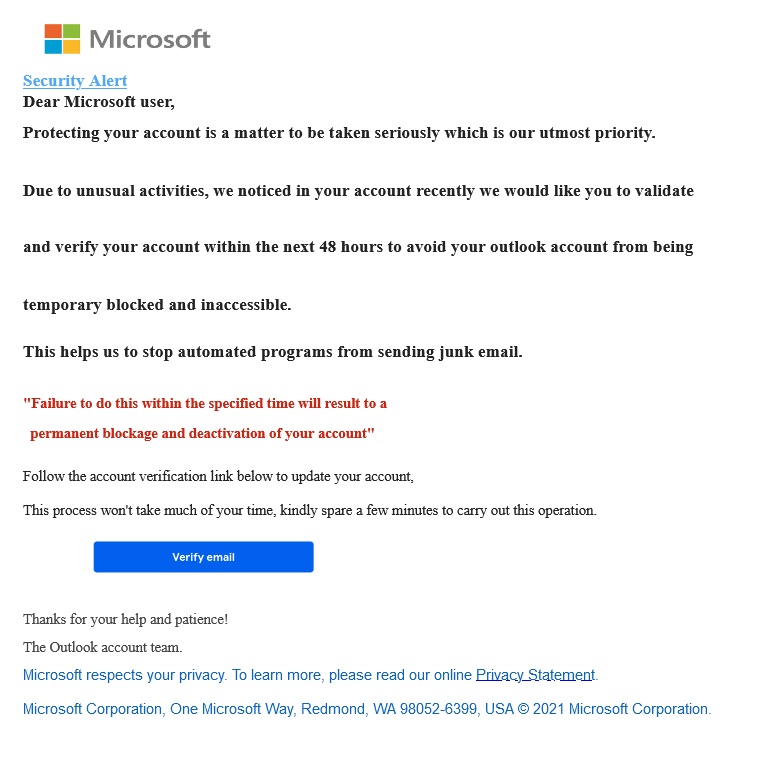
Phishing letter
The letter is basically a picture on a white background (so it blends in with Outlook’s default interface). Here is a typical example of a phishing letter of this sort:
As always, we should consider whether each element of the message is appropriate, normal, and plausible. One aspect that leaps out is the format. There is no legal reason for this (or just about any) letter to be a picture. In particular, automatically generated letters such as account verifications use text. Checking whether the letter is a picture or text is simple: Hover over a hyperlink or button and see if the mouse cursor changes — with normal text, it will. In this case, however, clicking anywhere on the picture will open the hyperlink because the target URL is attached to the picture, so basically the whole picture is one button/hyperlink.
If any doubt remains, try highlighting a portion of the text or resizing your mail client window. If it’s a picture, you won’t be able to highlight any words in it, and resizing the window won’t cause the lines of text to rewrap or change in length.
The general style of the letter hardly adds credibility — the varying fonts and line spacing, improper use of punctuation, and awkward language are all signs of a scam. Of course, people make mistakes, but Microsoft’s templates don’t tend to have any. If you see this many blatant errors in any letter, it is most likely phishing.
One last thing: The claim that the account must be verified within 48 hours should also ring an alarm bell. Scammers often try to rush users into taking careless actions.
Phishing site
Moving past the letter, the site to which it refers looks even less convincing. A legal site belonging to Microsoft would be hosted on a Microsoft domain, but the “Create your website with WordPress.com” banner clearly communicates that the site was built on the free hosting platform WordPress.
On the whole, a website of this design looks like a real one — maybe 25 years ago. Here’s the modern Microsoft services sign-in page, for comparison: https://login.microsoftonline.com/.
How to stay safe
A reliable protective solution detects phishing letters based on several factors, not text analysis alone. We therefore recommend using modern mail protection mechanisms such as those in Kaspersky Security for Microsoft Office 365.
Every employee workstation and connected device needs additional security as well, to serve as an extra barrier against phishing and other tricks.
Finally, don’t forget our constant refrain: Keep promoting cybersecurity awareness among staff through training. The better people understand the ways of modern cybercriminals, the less likely they are to fall victim to phishing.
 phishing
phishing


 Tips
Tips