We recently posted that ransomware is giving way to miners at the top of the online threat rankings. In line with this trend, the Trojan ransomware Rakhni, which we’ve been watching since 2013, has added a cryptocurrency mining module to its arsenal. What’s interesting is that the malware loader is able to choose which component to install depending on the device. Our researchers figured out how the updated malware works and where the danger lies.
Our products spotted Rakhni in Russia, Kazakhstan, Ukraine, Germany, and India. The malware is distributed mainly through spam mailings with malicious attachments. The sample that our experts studied, for example, was disguised as a financial document. This suggests that the cybercriminals behind it are primarily interested in corporate “clients.”
A DOCX attachment in a spam e-mail contains a PDF document. If the user allows editing and tries to open the PDF, the system requests permission to run an executable file from an unknown publisher. With the user’s permission, Rakhni swings into action.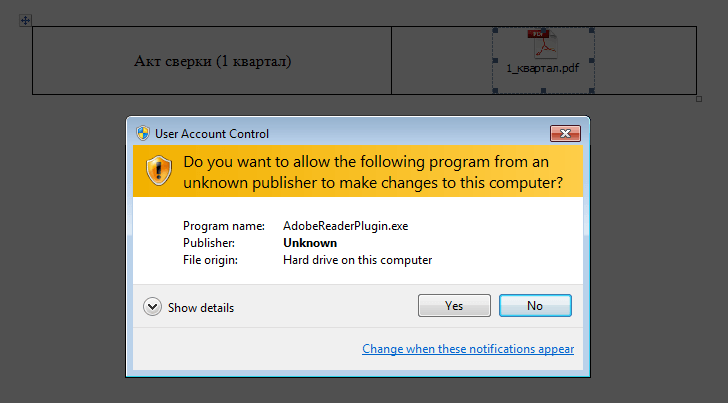
Like a thief in the night
When it’s started, the malicious PDF file appears to be a document viewer. First, the malware shows the victim an error message explaining why nothing has opened. Next, it disables Windows Defender and installs forged digital certificates. Only when the coast seems clear does it decide what to do with the infected device — encrypt files and demand ransom or install a miner.
Finally, the malicious program tries to spread to other computers inside the local network. If company employees have shared access to the Users folder on their devices, the malware copies itself onto them.
Mine or encrypt?
The selection criterion is simple: If the malware finds a service folder called Bitcoin on the victim’s computer, it runs a piece of ransomware that encrypts files (including Office docs, PDFs, images, and backups) and demands a ransom payment within three days. Details of the ransom, including how much, the cybercriminals kindly promise to send by e-mail.
If there are no Bitcoin-related folders on the device, and the malware believes it has enough power to handle cryptocurrency mining, it downloads a miner that surreptitiously generates Monero, Monero Original, or Dashcoin tokens in the background.
Don’t be a victim
To avoid getting infected by Rakhni and having real damage inflicted on your company, be very wary of incoming messages, especially ones received from unfamiliar e-mail addresses. If you’re in any doubt at all about whether to open an attachment, don’t. Also, pay close attention to operating system warnings: Don’t run apps from unknown publishers, especially if the names sound similar to popular programs.
In the fight against miners and cryptors in the corporate network, you won’t go wrong by taking these measures:
- Train your information security staff and regularly check their know-how. If you need help with that, our experts can arrange it for you.
- Make backup copies of sensitive data on a separate storage medium.
- Use reliable security solutions with behavioral analysis — for example, Kaspersky Endpoint Security for Business.
- Regularly probe your corporate network for anomalies.
Even if you don’t use Kaspersky Lab’s corporate solutions, that’s no reason to leave data to ransomware actors. We have a dedicated solution — the Kaspersky Anti-Ransomware Tool — that can augment the security products of most third-party vendors. It uses the latest behavioral detection technologies and our cloud mechanisms to hunt for ransomware.
 ransomware
ransomware

 Tips
Tips