In recent years, cybercriminals have stepped up their efforts to get hold of users’ money. Credit card numbers, login details for online banking, passwords and codes – all this and more is being collected by malware. But who exactly is being targeted? In May 2012, Kaspersky Lab conducted a survey in collaboration with O+K Research and found that 69% of respondents use online banking services, so, clearly, the majority of Internet users are potential targets.
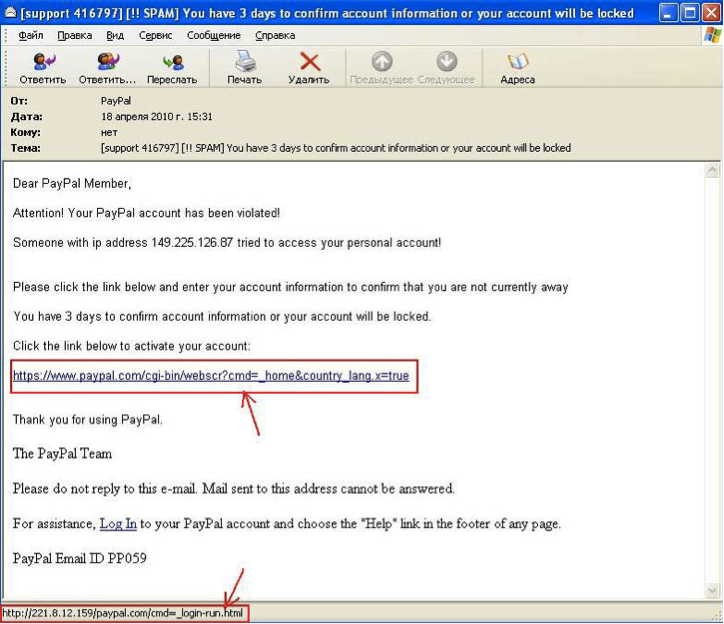
An attacker can get access to financial information using several social engineering techniques. A single banking Trojan designed to steal credentials is capable of cleaning out your online bank account. One of the most popular methods of data theft is a mass mailing that looks like it has been sent by a bank. The contents vary depending on the fraudsters’ capabilities and imagination. Typically, the fake message is an exact copy of an official email sent on some pretext that lures the recipient into logging on to the bank’s official website. If the link in the message is clicked, the website opens after a short delay. That delay is the time needed to redirect the link to an infected page where a malicious object is secretly downloaded onto the victim’s computer before carrying on to the bank. Any data subsequently entered on the banking site will be stolen by the malware.
In other cases the link may lead to an exact copy of the bank’s site hosted on a domain that looks very similar to the official one. Although the system is not infected, any data entered on the phishing site falls into the hands of cybercriminals.
A malicious object infecting the system can secretly download and install additional modules, e.g. a keylogger to intercept data entered via the keyboard. Of course, this can be any kind of data, including those used to authenticate online banking transactions. Cybercriminals are especially fond of Trojans designed to search and extract bank information from the files stored on a computer. Other Trojan programs only work when you connect to your online banking system: they can redirect you to a malicious site instead of the official bank website or modify the web page by adding their own fields to the original site downloaded in the browser. This was the case with the famous ZeuS Trojan which infected 3.6 million computers in the US in 2009.
During the first few months of 2012 Kaspersky Lab detected slightly more than 15,000 malicious programs designed to steal banking credentials. Should any of them get into your system, the chances are your money will soon be leaving your account.
In order to protect their customers from cybercriminals, banks use several tools. First of all, secure, encrypted connections protect data from being intercepted during transactions. However, this does not help if your computer is already infected. Secondly, some banks use two-factor authentication instead of the standard password authorization. In this case, you have two passwords: a constant password to log in to the system and a one-off password to confirm each individual transaction. So, even if the fraudsters succeeded in stealing your login and password, they won’t be able to use your money. Unfortunately, cybercriminals have found a way to bypass this sort of protection. The mobile version of ZeuS (known as ZeuS-in-the-Mobile, or ZitMo) is designed to intercept text messages containing a one-off code (mTAN) by infecting your smartphone in addition to your computer.
As you can see, cybercriminals are developing increasingly sophisticated tools to steal financial information, while the banks’ security measures can’t provide enough protection on their own. To ensure safe and secure operations with online banks, comprehensive security software is required for laptops, PCs and mobile devices. Kaspersky Internet Security 2013 is recommended for laptops and PCs, while Kaspersky Mobile Security or Kaspersky Tablet Security – depending on what Android-based device needs protection – is recommended for mobile devices.
 kaspersky internet security
kaspersky internet security


 Tips
Tips