If December means predicting the new year in the security world, then it also means recapping the year that’s about to end. And that’s just what Kaspersky Lab’s Global Research and Analysis Team has done with this list of 2014’s ten emergent trends in the Internet security industry.
A Bevy of Advanced Persistent Threats
APT groups certainly didn’t slow down in 2014. Kaspersky Lab researchers published their own research on at least six distinct attack groups. There was the Spanish language “Careto” campaign back in February, which had been active for some seven years prior. Careto (AKA the Mask) relied on an easily modifiable, cross-platform malware kit designed to steal sensitive information from government agencies, embassies, energy companies, research institutions, private equity firms and activists in 31 countries around the world.
There was also the versatile Epic Turla campaign that emerged a month or so later in March, which targeted its victims with a series of zero day exploits on Adobe Acrobat, Windows XP and Microsoft server 2003, as well as a number of watering hole attacks targeting vulnerabilities in Java, Adobe Flash and Internet Explorer.
In June another group made off with a half million Euros in a single week after targeting the clients of a large European bank as part of a campaign dubbed “Luuuk.” Kaspersky Lab wasn’t able to obtain any malware samples in this attack, but they believe that it stole usernames, passwords and one-time passcodes, which were used to check victim account balances and perform transactions automatically.
Later in June, a new version of the “MiniDuke” campaign, called “CosmicDuke,” emerged, targeting governments, diplomatic agencies, energy firms, military groups and telecom operators. Oddly, the campaign also targeted criminal groups involved in trafficking illegal substances such as steroids and growth hormones.
#Kaspersky launches a project that chronicles all of the #ATPs the company has investigated https://t.co/9gj6AiRVoo pic.twitter.com/HHbRUDVC0o
— Kaspersky Business (@KasperskyLabB2B) December 11, 2014
Kaspersky Lab reported on the Crouching Yeti attack group in late July as it sought intellectual property and other sensitive information from targets in Syria, Turkey, Saudi Arabia, Lebanon, Palestine, the United Arab Emirates, Israel, Morocco, France and the United States, from IP blocks in Syria, Russia, Lebanon, the United States and Brazil.
Another key campaign was DarkHotel, reported on in November, in which attackers infected the networks of hotels in the Asia-Pacific region in order to install malware on the machines of corporate execs as they travelled around the world.
Big Vulnerabilities and the Internet of Things
Kaspersky Lab researchers saw an unsettling convergence of bugs affecting nearly everyone online and the hyper-adoption of so-called “Internet of Things” devices that are closer to our lives than the traditional computer. Widespread bugs like Heartbleed and Shellshock (AKA Bashdoor) existed in an unknown number of systems for long periods of time. Their full impact is now, and will likely remain, unknown.
#KLReport: the modern home is shockingly vulnerable to hacking
Tweet
While adoption rates of seemingly futuristic devices, like connected home appliances and IP-enabled thermostats, are still relatively low, modern homes are certainly loaded with connected devices like Smart TVs, routers, mobile devices, traditional computers and gaming systems. These devices contain vulnerabilities just like any operating system, software or application, and these vulnerabilities, like Heartbleed and Bash, could remain on a device for years without the user even being aware. Problematically, these devices are often more difficult to update than traditional computers and software platforms. As Kaspersky’s David Jacoby realized earlier this year, the modern home is shockingly vulnerable to hacking.
A fascinating story how @JacobyDavid hacked his smart home https://t.co/ckTyeMVLUp pic.twitter.com/q4LiqsBnA4
— Eugene Kaspersky (@e_kaspersky) September 25, 2014
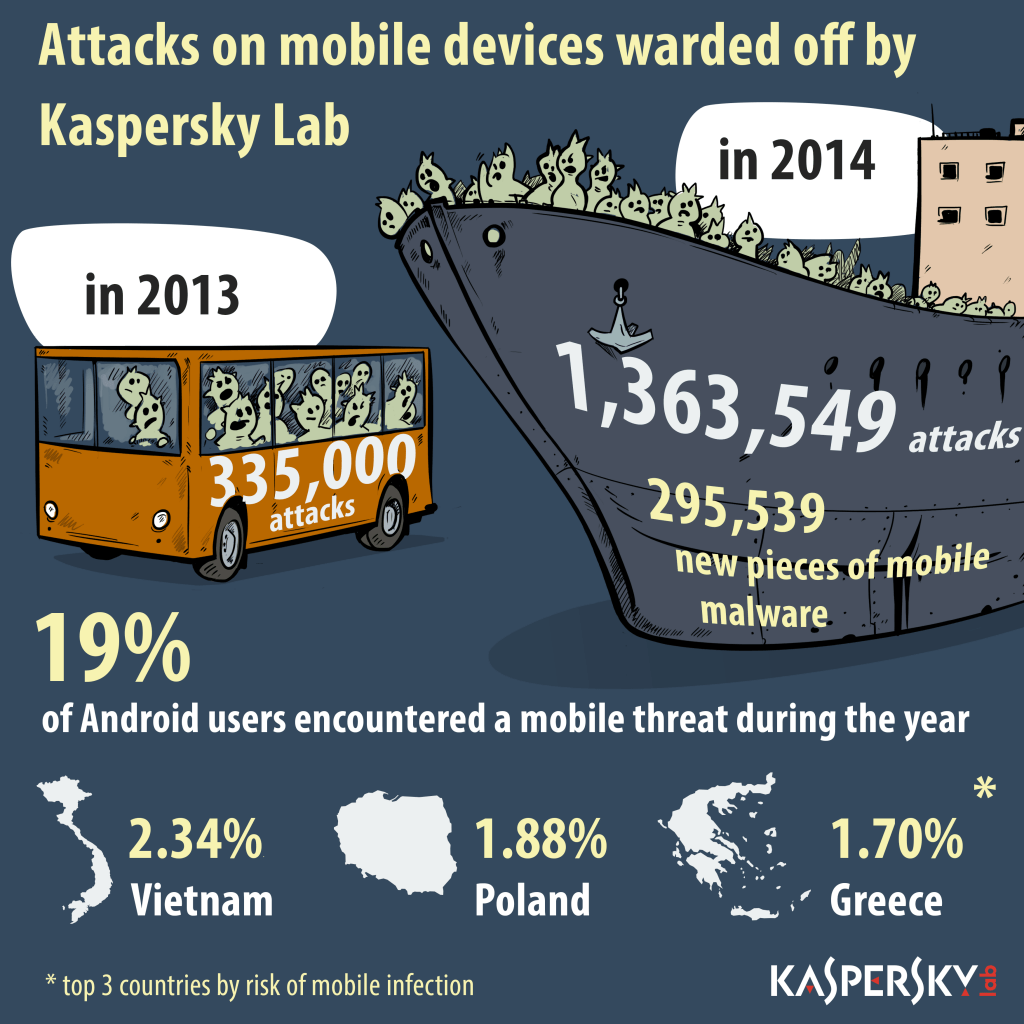
Mobile Malware Still on the Rise
From 2004 through 2013, Kaspersky Lab analyzed some 200,000 mobile malware samples. This year alone, Kaspersky Lab has analyzed 295,539 samples. Most mobile threats are designed to pilfer banking credentials and, ultimately, steal money. However, in 2014, Kaspersky researchers note that mobile ransomware and fake antivirus malware emerged as well. Furthermore, Apple’s iOS mobile operating system was targeted by the WireLurker malware, which is — by all accounts — the first piece of malware capable of targeting iOS devices that aren’t jailbroken.
Speaking of Ransomware…
Whether it was blocking access to user devices or encrypting all of the files on an infected machine, ransomware had a big year. There was CryptoLocker, CoinVault, ZeroLocker and a number of other pieces of malware that attempted to make users pay money, typically bitcoin, in order to make their computers work again. Some experts believe ransomware has a bright future, but there are certainly ways to combat it:
“Ransomware operations rely on their victims paying up,” the Kaspersky research team explains. “Don’t do it! Instead, regularly back up your data. That way, if you ever fall victim to a ransomware program (or a hardware problem that stops you from accessing your files) you will not lose any of your data.”
ATM Skimming
Mechanisms and malware designed to either steal money or sensitive consumer financial information from ATMs are not new by any means, but skimmers had a big year in 2014. One particularly sophisticated example was the “Tyupkin” malware. Criminals in Asia, Europe and Latin America first gained physical access to ATMs before loading Tyupkin onto them via CD. After this, the infected machines rebooted and fell under the control of the attackers. From there, the criminals behind the scheme sent mules along to enter unique codes into the ATMs and dispense cash, but only at certain times in order to prevent the scam from being recognized as such.
Can ATMs get #malware infection & give away cash? Yes, here is a real case: https://t.co/xOzKZ0h3kz pic.twitter.com/4hb8NrbhYE
— Eugene Kaspersky (@e_kaspersky) October 7, 2014
“The upswing in ATM attacks over recent years is a natural evolution from the more well-established method of using physical skimmers to capture data from cards used in ATMs that have been tampered with. Unfortunately, many ATMs run operating systems with known security weaknesses. This makes physical security even more important; we would urge all banks to review the physical security of their ATMs.”
Every Bug a Zero Day for XP
Microsoft no longer provides support for Windows XP. This means that on Microsoft’s monthly patch Tuesday bulletins, where the company releases fixes for security vulnerabilities, there are no longer any fixes for Windows XP bugs. In other words, every Windows XP vulnerability from April 8, 2014 until the end of time is a zero day. This wouldn’t be such a big deal, however, Windows XP still commands nearly 14 percent of the desktop operating system marketshare. Beyond the consumer, devices like ATMs, critical infrastructure systems, medical devices and even the computers at many banks and doctors’ offices are still running XP and handling highly sensitive data and operations at the same time. So, while XP may have lost support in 2014, it’s likely to remain a popular target moving forward.
#KLReport: every single Windows XP vulnerability from April 8, 2014 until the end of the world is a #zeroday
Tweet
The Tor Network
The anonymous browsing service Tor really hit the mainstream in 2014. Researchers here note that Tor usage spiked this year, in large part due to privacy concerns in the wake NSA whistleblower, Edward Snowden’s government surveillance revelations. Unfortunately, the Tor network is also a hotbed for criminal activity. Servers can operate on Tor too and are known as “hidden services.” These hidden services offer marketplaces for all sorts of illegal goods and services. In fact, if you can dream it, you can probably buy it browsing on Tor in an underground marketplace.
Morally Ambiguous Software
“Unfortunately, software isn’t neatly divided between good and bad programs,” Kaspersky’s researchers wrote. “There’s always the risk that software developed for legitimate purposes might be misused by cybercriminals. At the Kaspersky Security Analyst Summit 2014 in February we outlined how improper implementation of anti-theft technologies, residing in the firmware of commonly used laptops and some desktop computers, could become a powerful weapon in the hands of cybercriminals.”
Indeed, I wrote about the mysterious Computrace backdoor at the Black Hat security conference this year, and it serves to demonstrate an interesting phenomenon: people with ill intentions can exploit the legitimate purposes of well-meaning software.
However, there is another side of this coin: “legal” software that performs ethically questionable behavior. One such example was the “Remote Control System” (RCS) developed by an Italian company called Hacking Team. RCS and platforms like it are technically legal, but despotic regimes use these tools to spy on dissidents and civil rights groups both within their borders and beyond.
Kaspersky Lab’s researchers stand by their policy to detect and remediate any malware attack, regardless of its origin or purpose.
Privacy vs. Security
We continue to struggle with the desire for privacy but the failure to maintain it in part because we don’t want to be encumbered by the inconvenience of security. The iCloud celebrity photo-leak from earlier this year is a great example: no photo would have been leaked had iCloud accounts been protected with strong, unique passwords. Furthermore, had Apple offered universal two-factor authentication, and had the victims of this breach deployed that protection, then there would not have been a celebrity photo leak to begin with. However, deploying a strong password or enabling two-factor authentication puts the security burden on an unreliable party: the consumer.
http://instagram.com/p/vRJXxkP0Dm/
Botching security and then blaming the consumer is ‘lame’ and the tech companies that offer online services need to build security in. That’s why Apple’s and Google’s announcements about default mobile device encryption and Twitter’s new “Digits” authentication service, which sends one time passwords to users via text message, were promising steps in the right direction for security in 2014.
Law Enforcement Learning to Catch Cybercriminals
Last but certainly not least, 2014 offered promise for law enforcement agencies that, despite the bad surveillance-related press, are tasked with a thankless and incredibly difficult job. Kaspersky’s GReAT researchers recounted the successes that international police forces saw this year.
Kaspersky Lab to provide its products, intelligence & ongoing support to INTERPOL and its 190 members http://t.co/Y8fbL1eqzu
— Eugene Kaspersky (@e_kaspersky) September 30, 2014
A coalition of police forces from all around the world came together to takedown the “GameOver Zeus” botnet, which, to that point, was one of the largest crimewave kits on the market. Criminals used GameOver not only for its intended purpose as a credential stealing banking trojan, but also as a distribution platform for the infamous crypto locker malware.
Kaspersky Lab also listed its contribution to a broader law enforcement-backed takedown of the “Shylock” trojan, which deployed man-in-the-browser attacks to steal banking login credentials from online banking customers. More recently, “Operation Onymous” resulted in the takedown of dark markets running within the Tor network.
 APT
APT