As you know, Google is not just a search tool, but multiple services used by billions of people every day: Gmail, Calendar, Google Drive, Google Photos, Google Translate, the list goes on. And they are all integrated with each other. Calendar is linked to Gmail, Gmail to Google Drive, Google Drive to Google Photos, and so on.
It’s all very handy — register once and away you go. And there’s no need to mess around moving files and data between services; Google does everything for you. The downside is that online fraudsters have learned to exploit the convenience of Google services to send spam or worse.
Spam through Google services: Calendar, Photos, Drive, Storage, Analytics, and Forms
The spammer’s main task is to bypass the spam filter and deliver e-mail to your inbox. As it happens, Google services often send e-mail notifications to Gmail inboxes — and Google’s antispam module avoids flagging notifications from its own services as spam. With that in mind, let’s look at which Google services spammers use — and how.
Spam in Google Calendar
Naturally, if someone uses Google Calendar to arrange a meeting with you, you receive notifications about it. Well, spammers have recently taken to making appointments en masse.
Because Google Calendar is designed to let anyone at all invite you to a meeting, both Calendar and Gmail (which receives the notification) are totally fine with any John Doe scheduling a meeting with you.
Spammers use the location and topic fields to convey the details to you. Usually, their spam details consist of a short bit of text stating that you are entitled to a cash payment for some reason, and a link that supposedly lets you receive it.
After that, everything’s about the same — either it’s a phishing link from which the cybercriminals try to get your bank card details (ostensibly to send you the money), or they ask for some sort of transfer fee to be paid before the money is sent. (You’ll never see a dime, obviously.)
Attackers are also adept at using Google Calendar to set up fake polls for which a reward is likewise offered. And there is nothing to prevent them from using this same loophole to distribute other types of spam or phishing, as well as malware.
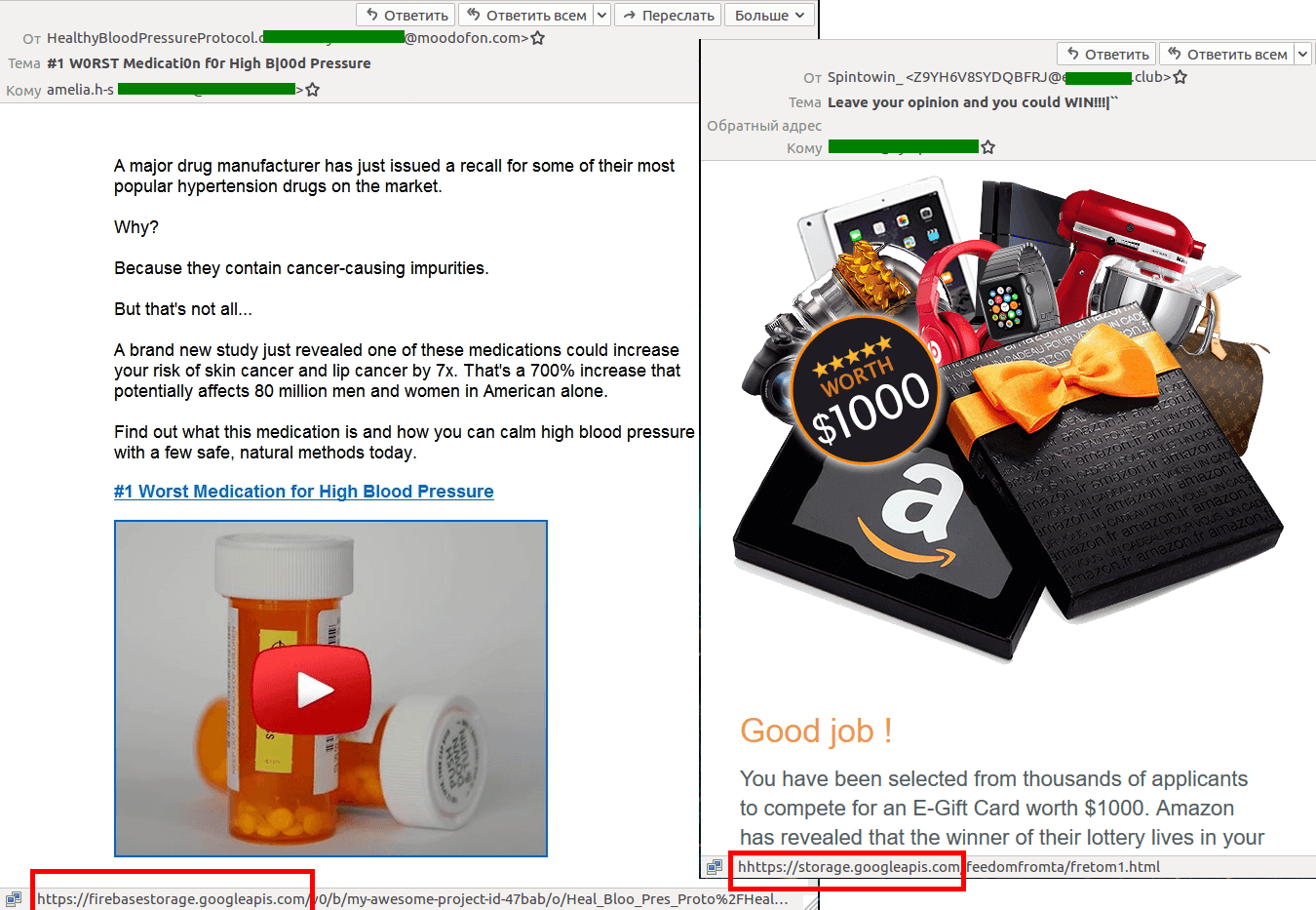
Spam in Google Photos
Scammers use Google Photos to share photographs that include comments about sudden large remittances that can be had by replying to the e-mail address supplied in the message. For the recipient, it looks like a harmless e-mail from Google Photos with the header “So-and-so shared a photo with you.”
A photo of a nonexistent check should immediately betray the scammers’ intentions. The check states that some commission fee will unlock a much larger amount. After the victim pays up, the scammers simply vanish into the ether.
Google Photos is great for cybercriminals precisely because it allows a picture and text comment to be placed in an e-mail notification with such an innocuous header that it is almost certain to be opened.
Spam in Google Forms
Scammers actively use Google’s versatile tool for creating forms and polls to harvest personal user data and send unsolicited commercial offers.
Its convincing-looking data collection forms helped make Google Forms another darling of scammers and phishers. Victims obligingly fill out the forms with personal data, card details, and the like.
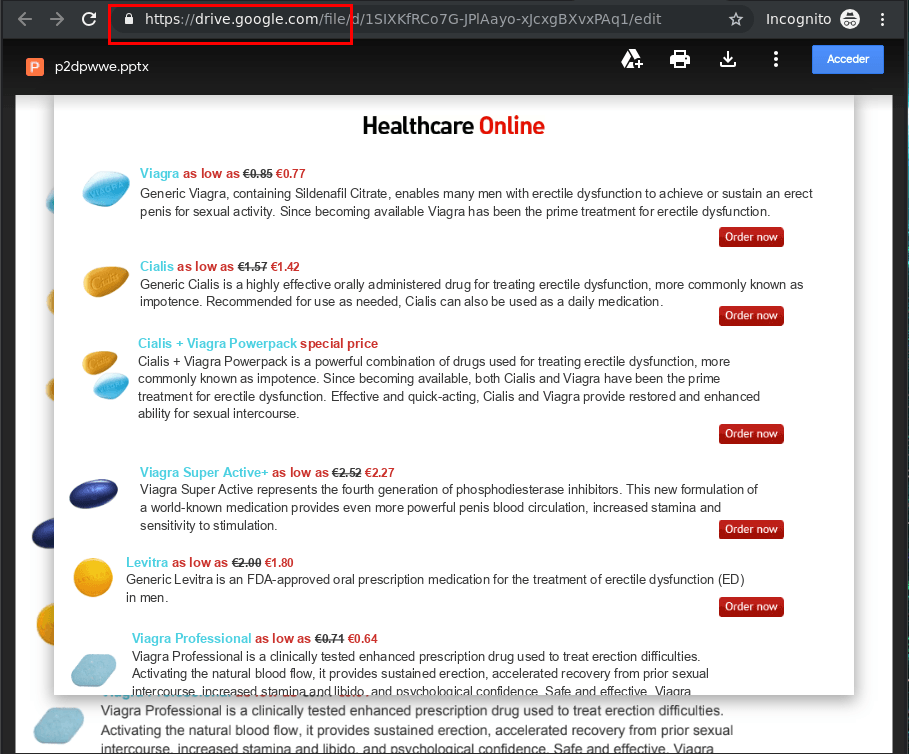
Spam in Google Drive and Google Storage
Our quarterly spam and phishing reports repeatedly warn users that cybercriminals have long been using cloud storage to hide their illegal content. After all, it is extremely difficult for spam filters to determine whether an e-mail is fraudulent based on a unique link inside it consisting of a random set of symbols.
In this way, virtually anything can be delivered to the recipient, including malware, phishing pages with data collection forms, and annoying ads. Most of the time, such links point to cloud documents (text files, spreadsheets, presentations) with a more detailed description and new links to the “end product.”
Google Storage is another repository of spam resources. These include links with redirects to fake landing pages and various images for use in spam mailings.
Spam in Google Analytics
Such spam has made its way into other popular Google services, too. Among them are Google Hangouts and even notifications from Google Ads and Google Analytics. In the latter case, users receive a message with an attached visitor statistics PDF report for an unfamiliar website.
Analytics allows this file to be accompanied by text and a link, a fact exploited by cybercriminals. Here they can target business users, since these services are actively used by website owners.
Spam through popular services — not only Google’s problem
It is not only Google services that spammers love. Scam messages and comments appear in huge numbers in all commonly used social networks and services (Facebook, Twitter, Instagram) — anything publicly accessible where users can add some text to service messages.
Another problem is that many services are linked to users’ mobile phones, which means that each new notification not only arrives by e-mail, but is also duplicated as a pop-up alert on the gadget screen. Irritating notifications crawling out from everywhere make the user less attentive and more likely to tap or click a fake link without looking.
The main problem is that messages sent through a legal service are assigned its standard headers, so spam filters often view them as harmless. And spam subjects vary widely, so interception requires a high threshold level in the spam filter, which can lead to excessive false positives. Spammers take advantage of this to exploit public services for their own purposes.
How to guard against spam distribution through Google and other popular services
Unfortunately, there is no silver bullet against such spam. The settings required depend on the service, and in most cases they reduce its usability.
For example, in Google Calendar, it is possible to disable automatic adding of events until invitations are accepted, but this also affects events that are of genuine interest. However, the spam in this tool is perhaps the most intrusive, so it makes sense to do so.
In fairness, we should mention that Google does a lot to combat spam and keep scammers out. But as Google itself rightly notes, the struggle against spam is never-ending. That means as soon as spamming through Google services in its current form is defeated (which it surely will be), cybercriminals will find other loopholes.
The most important thing is to be attentive.
- Do not open messages from unknown senders.
- Never accept invitations from people you don’t know.
- Do not tap or click links in messages you weren’t expecting.
- And install a reliable security solution with an antispam module to filter out at least some of the spam that wriggles through Google’s filter.
 spam
spam






 Tips
Tips