Disk and File Encryption
Protecting users of Kaspersky Endpoint Security (Business)
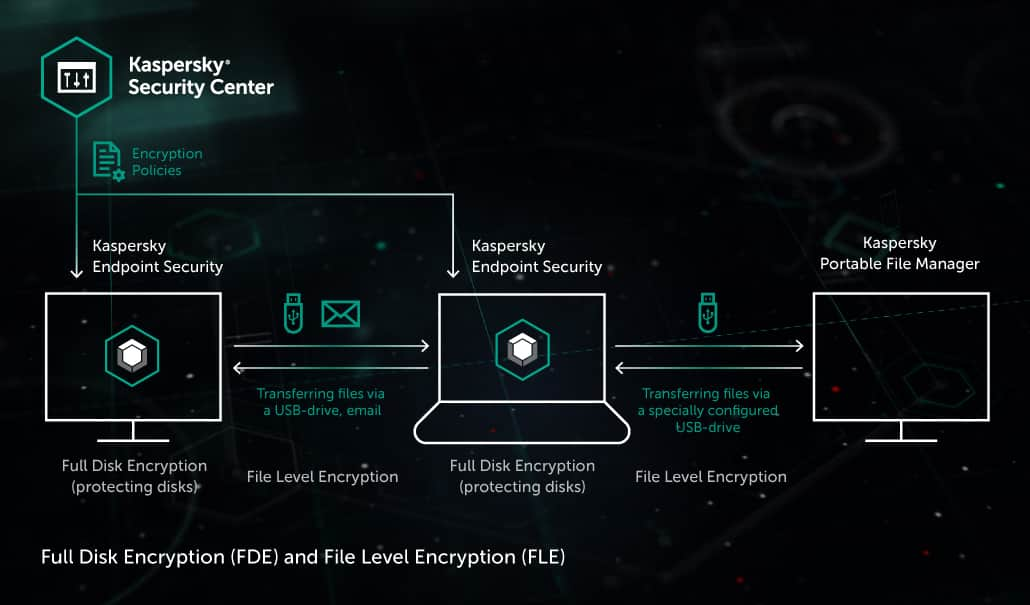
Kaspersky Endpoint Security for Windows has integrated tools for data encryption. They work according to policies distributed from Kaspersky Security Center, the administrator’s application for management of the corporate infrastructure protected by Kaspersky Lab security products.
Full disk encryption (FDE) prevents data leakage via loss of a laptop or a portable hard drive. When a disk is encrypted, unauthorized users cannot boot from it or read its data.
File-level encryption (FLE) protects files on the move when they are transferred in untrusted channels. The users that are allowed to access protected files according to encryption policies see them unencrypted.
Encryption policies
The administrators of Kaspersky Security Center can set encryption policies, which will enable encryption on corporate computers protected by Kaspersky Endpoint Security. Policies can differ between hosts, and policy compliance data is aggregated in a common report feed visible for administrators.
Policies can also be set for removable devices (flash drives, portable drives etc.) connected to a computer. For example, the device could be blocked until the user agrees to apply encryption to this device or to the specific types of files on it.
At file-level encryption, policies can define which files are to be encrypted, based on file extension or location on a disk. Once a matching file is detected on the computer, it gets encrypted.
Transparent encryption
Encryption doesn’t interfere with a typical user’s workflow: it doesn’t introduce new applications or changes in configuration of existing ones. Policies are applied automatically.
Encryption is transparent for applications: when a user is authenticated in the OS, applications see data on disks as if it is not encrypted, although it is. The encryption filter transmits data between applications and disks (a disk filter for FDE, and a file filter for FLE). It decrypts data coming from disks to applications and encrypts data that is coming back. Data is encrypted “on the fly”, immediately at read/write operations, and there is no data stored without encryption on the disk, even temporarily.
For some applications, encryption should not be this transparent. For instance, backup procedures that store a copy of an encrypted disk to keep it elsewhere should not store the backup data unencrypted. Therefore, the backing up application should copy the disk in its encrypted state. In this and other similar cases, transparent encryption can be centrally disabled by the administrator for particular applications.
Disk encryption mechanism (FDE)
The FDE mechanism encrypts entire disks on a computer.
FDE supports:
- Encryption of any disk types: HDD, SSD, flash-drives, etc. For SSD devices, FDE takes care to reduce the number of extra read/write cycles, increasing drive lifetime.
- Hardware acceleration of encryption (if the computer’s processor supports AES-NI).
- UEFI Secure Boot, a technology that protects computers at boot and guarantees that only trusted software is loaded, that OS and software start correctly without interference of any other processes.
Encryption keys. The disk encryption filter encrypts and decrypts data with a disk key. A separate key is created for each disk and stored on it in three encrypted copies. Even if the disk is damaged, and one key copy is destroyed, the disk can be accessed with another copy. If all three key copies on the disk are damaged, the access to the disk can be restored with the copy stored in Kaspersky Security Center. For this, when a disk key is created, its copy is securely sent to Kaspersky Security Center. Keys are never stored unencrypted on the disk.
User authentication and OS loading from an encrypted disk. The disk key stored on the disk becomes available to the encryption filter after a user’s authentication. A user can authenticate with a password, a USB token or a smart card. After successful authentication, the OS can boot from the encrypted disk.
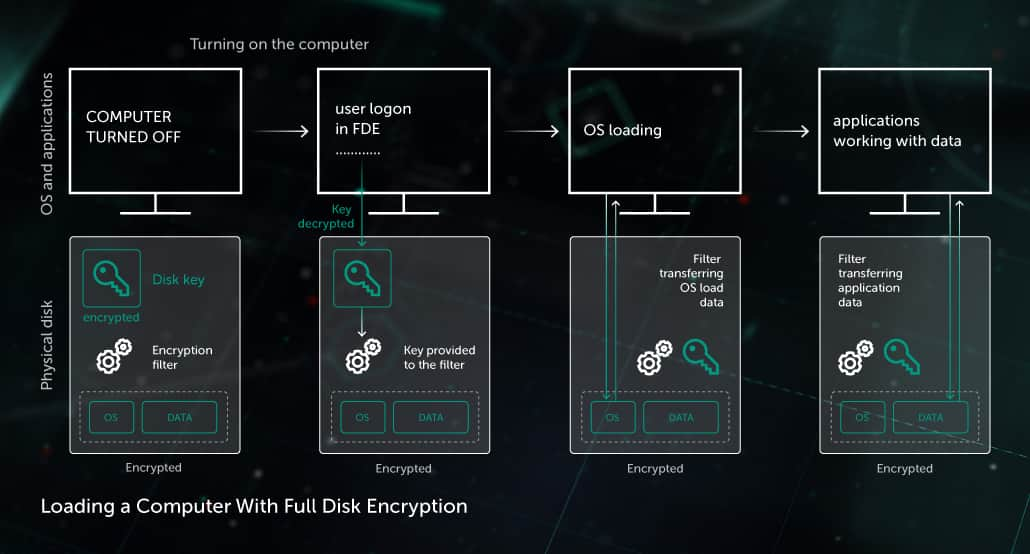
Encryption policy enforcement on a computer. When an encryption policy is applied on a computer, two processes start:
- Encryption on the fly is permanently enabled. This guarantees that all data written to the disk is encrypted since this moment. For this, disk encryption filter intercepts all read/write-to-disk processes.
- The disk encryption process is started, beginning the total encryption of the computer’s disks. When it is complete, disk encryption policy is fully enforced on the computer. Disk encryption may take several hours.
During disk encryption, users can work as usual, get the computer to the sleeping mode or turn it off: when it’s on again, the encryption will resume. The process is also robust to failures (e.g. power shutdown, OS failure). Failsafe encryption design guarantees that all the data will be eventually encrypted.
Access to encrypted files (FLE)
Access with Kaspersky Endpoint Security. When a user authenticates in the OS, applications on the computer that run on the behalf of the user get the access to the encrypted files, according to encryption policies.
For accessing files encrypted by other users, the Kaspersky Endpoint Security host agent requests the required decryption keys from the Kaspersky Security Center. For example, if an emailed file was encrypted by another user, the recipient’s host requests and receives a key from the Kaspersky Security Center (if policies allow access). This key works for accessing this file and other files encrypted on the same logical disk of that user. The key is cached, so there’s no need to request a new key each time a file is received that was encrypted on the same disk of the same user.
If there is no Internet connection, the recipient can get a key from Kaspersky Security Center via the standard challenge-response secure key exchange via open channels (e.g. a phone). Simply send a generated challenge code and then receive the response code.
Access without Kaspersky Endpoint Security. If this is allowed by encryption policies, users can configure their devices, so that encrypted files on these devices can be accessed on computers without Kaspersky Endpoint Security, by means of password authorization. When users configure such a device with Kaspersky Endpoint Security:
- The Kaspersky Portable File Manager application gets copied to the device. It securely stores keys for file access and encrypts / decrypts files.
- The user creates a password for accessing files on this device.
When a user connects a device and authorizes in Portable File Manager, encrypted files become available for reading and editing. Users can also encrypt new files to the device.
Protecting users of Kaspersky Total Security (Consumer)
Crypto Disk is a subsystem of Kaspersky Total Security that protects a user’s stored data with encryption.
With Crypto Disk, users create a virtual encrypted disk stored as a separate file. The disk is accessed with a password that is assigned when the disk is created. After authorization, the disk mounts as a local drive (e.g. “E:\”). A user can transfer a file with the encrypted disk to other users via devices, email, shared and cloud repositories, and grant other users access by giving them the password.
The disk is encrypted not on the password itself, but on an automatically generated key, which is available when the user is authenticated. This provides the option for a user to change a password without the need for re-encrypting the whole virtual disk.
Encryption module
FDE, FLE and Crypto Disk use the encryption module that utilizes the AES-256 encryption algorithm in the XTS mode. The encryption library is certified with:
- FIPS 140-2
- Common Criteria
 WHITEPAPER
WHITEPAPER
 WHITEPAPER
WHITEPAPERProtecting Sensitive Data with Kaspersky...